Secret Audit Documentation
Storing secrets unencrypted inside a codebase is usually a mistake or meant as a temporary fix. Unfortunately, production keys can stick around in the Git history longer than intended. Secret Audit helps ensure none of your team's secrets make it into your codebase in the first place.
Usage
- Connect your GitHub account or organization to the Secret Audit app.
- Select repositories to monitor for unintentional secret exposure.
- Rest easy that Secret Audit will help your team keep secrets, secret.
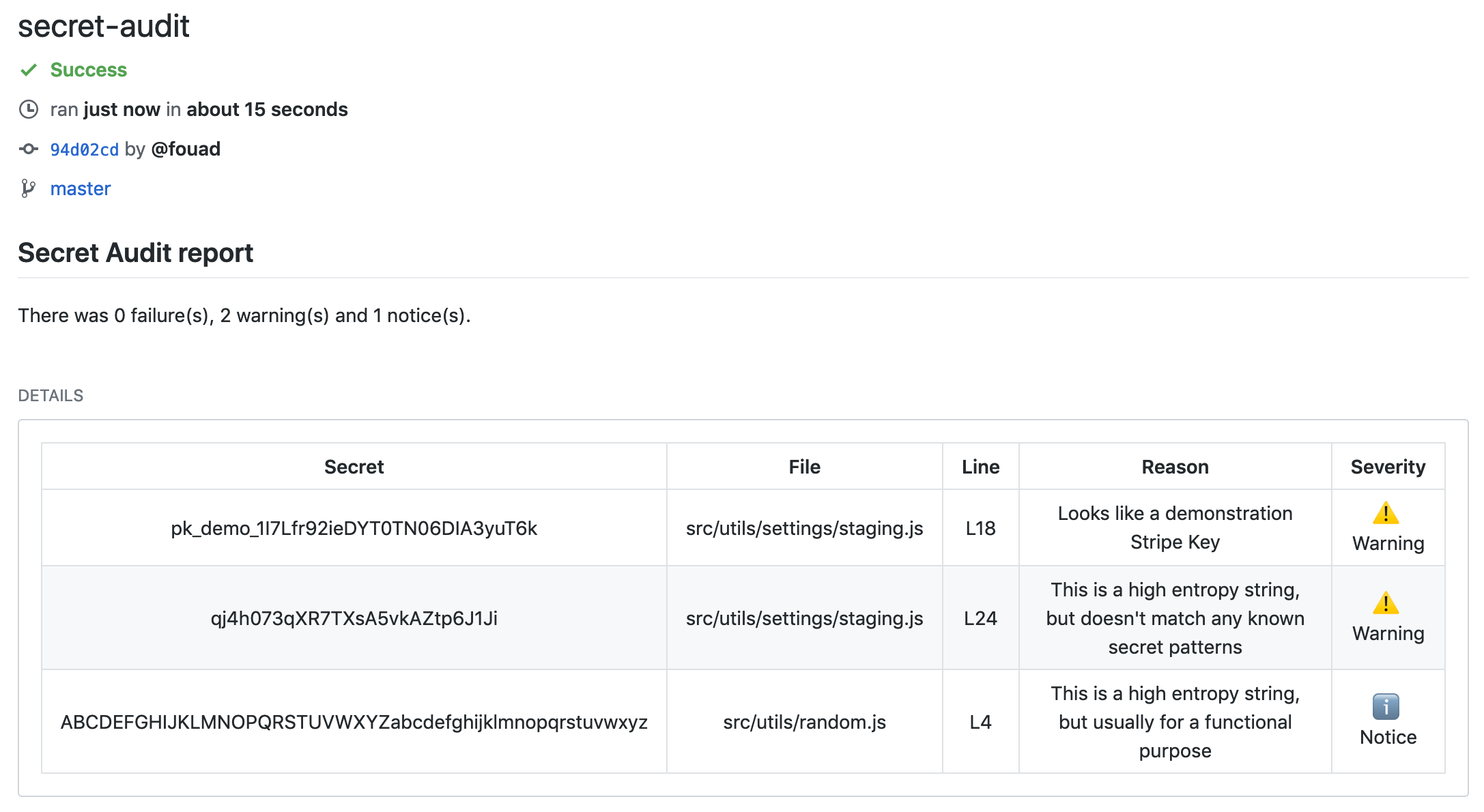
If you have a key that's been exposed, you'll see a screen like this:
If you're thinking, "Wait, I already deleted that secret!" The git commit log keeps old versions around by storing them as git objects.
You have two options: remove the secret from git history (recommended) or add a config file to ignore those secrets (paid plans only).
Why is removing the secret from git history recommended?
Once a key is in your git history, it's stuck there forever.
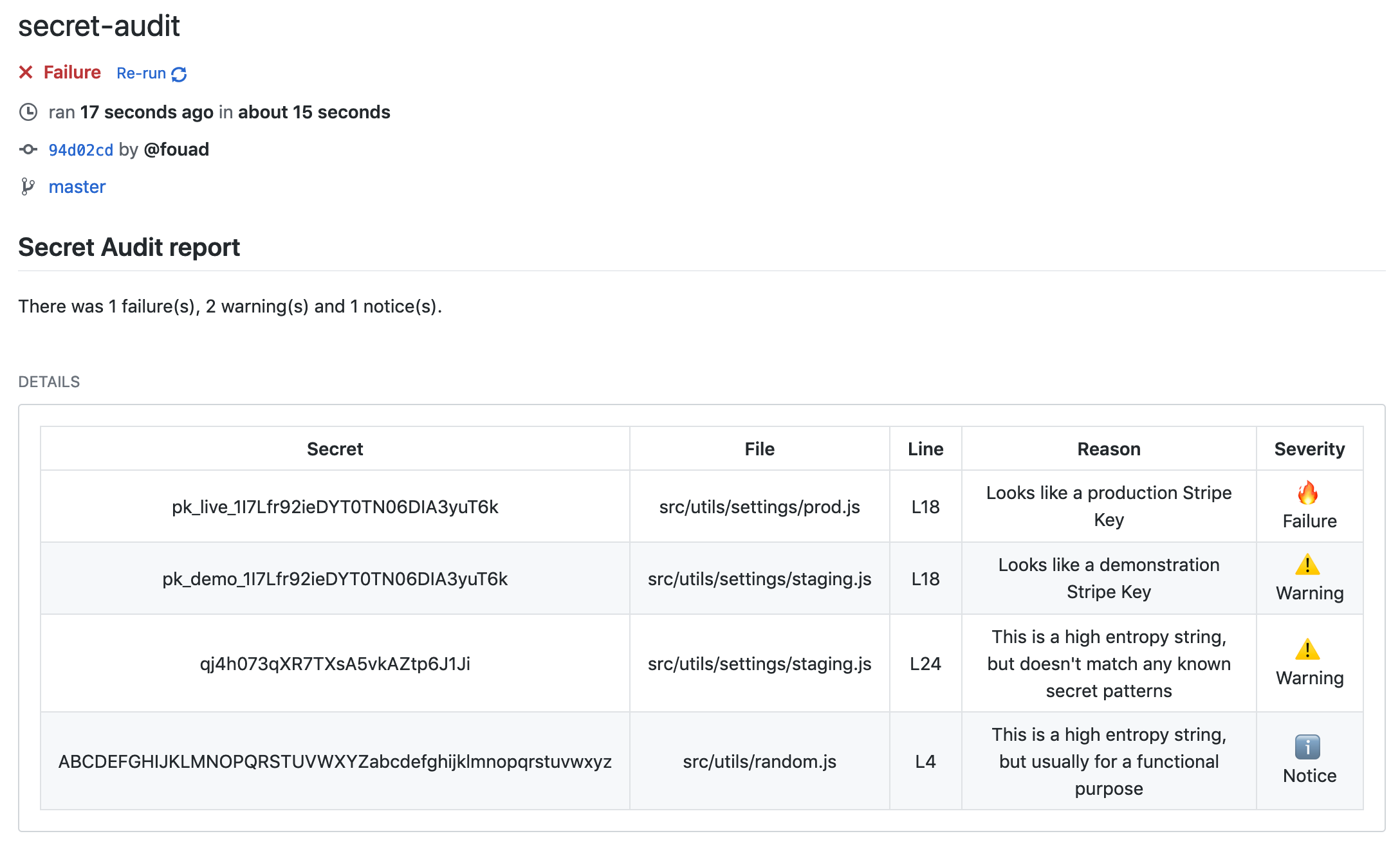
Now that you've removed or ignored the secret, you can re-run the check and should see this screen: