Easiest way to find and remove secrets from your codebase
Why care about secrets?
Developers often add API secrets to their code to access external services or sensitive data while developing.
Sometimes, those keys to sensitive data mistakenly end up in public deploys bad actors to abuse. Mistakes like this happen every year.
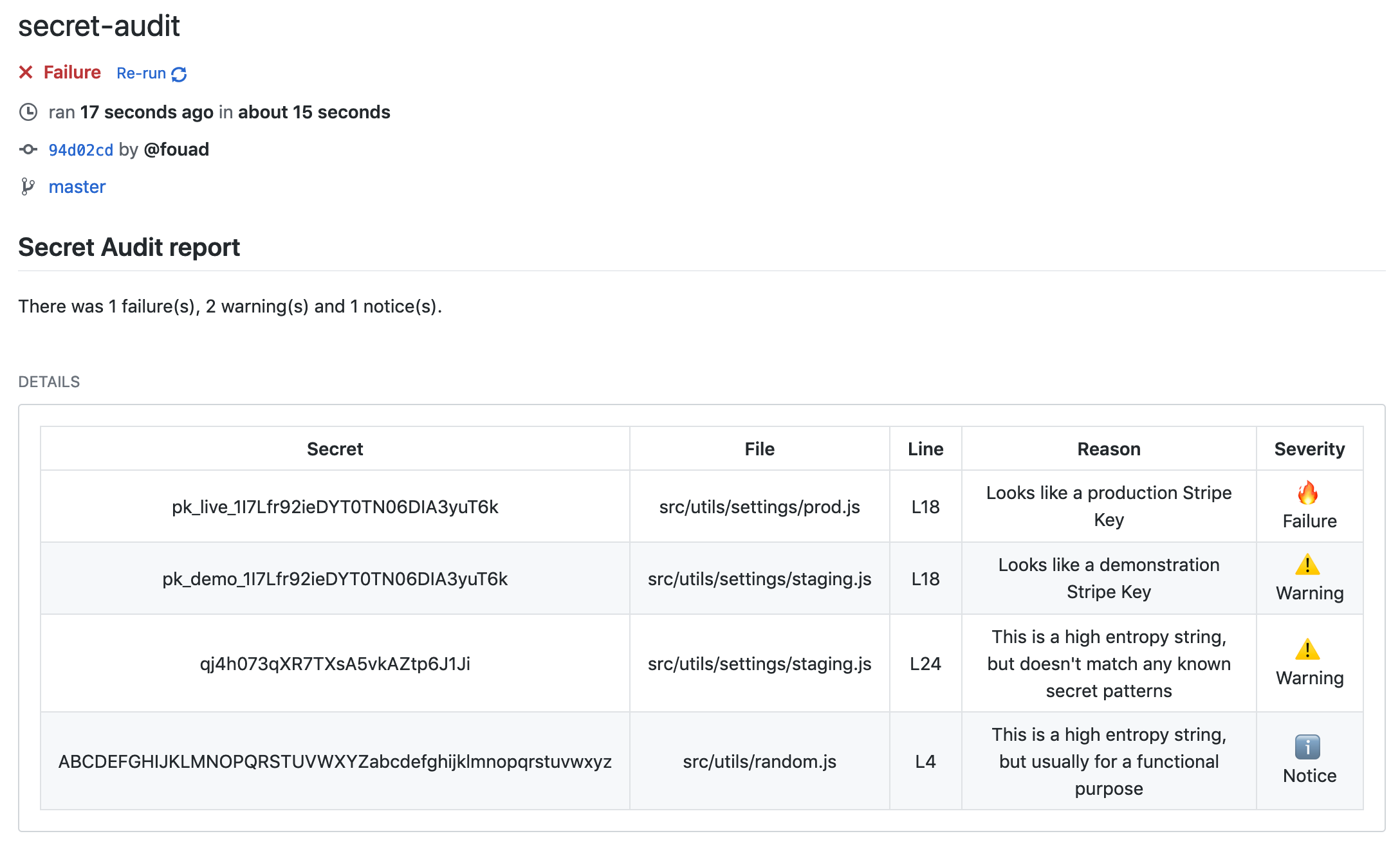
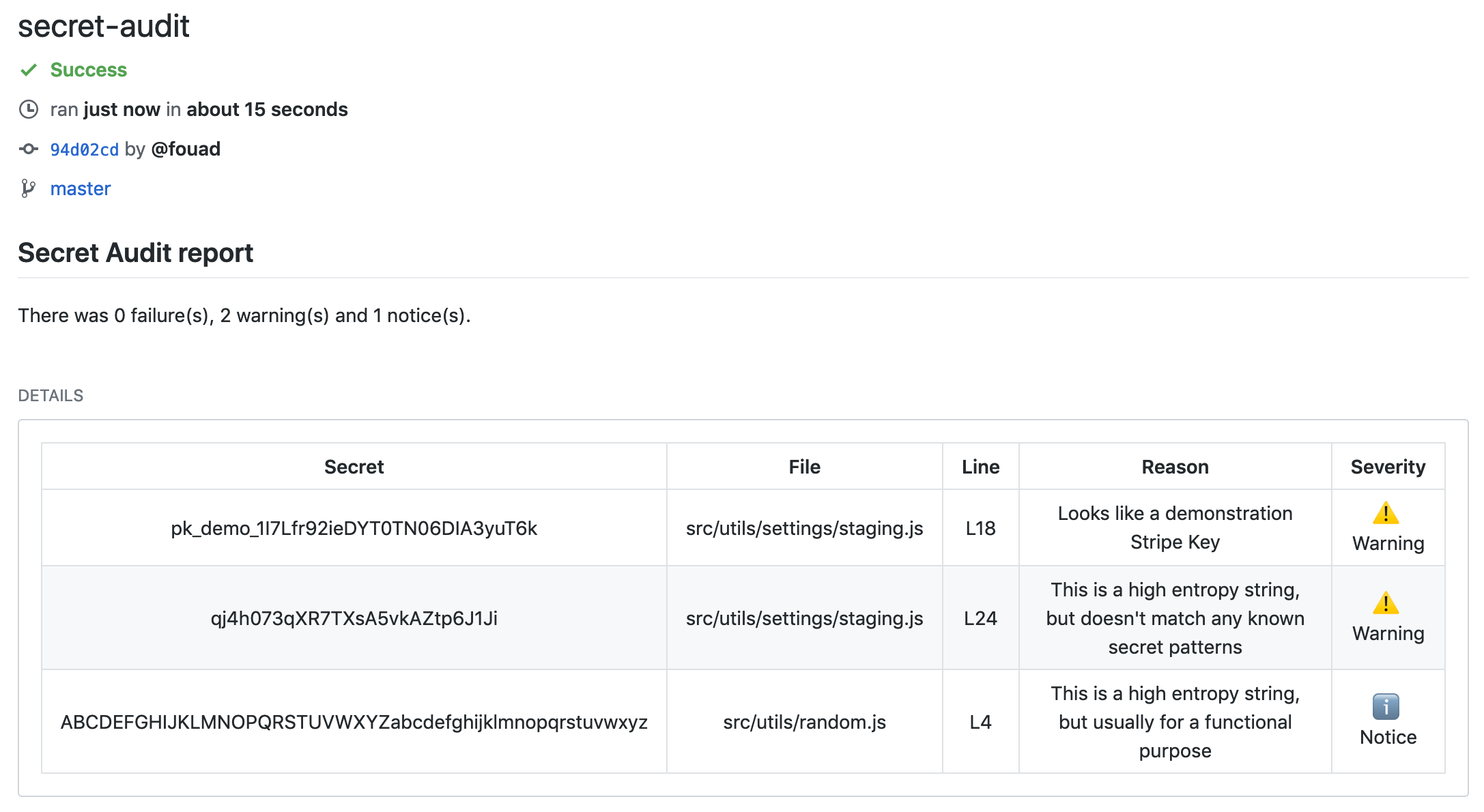
Secret Audit automatically detects then alerts developers and security teams before the API secret becomes public.
There are over 2.3 million public repositories with Google API keys.
Check if one of them is yours →
How it Works
1.
First, connect your GitHub account or organization to the Secret Audit app.
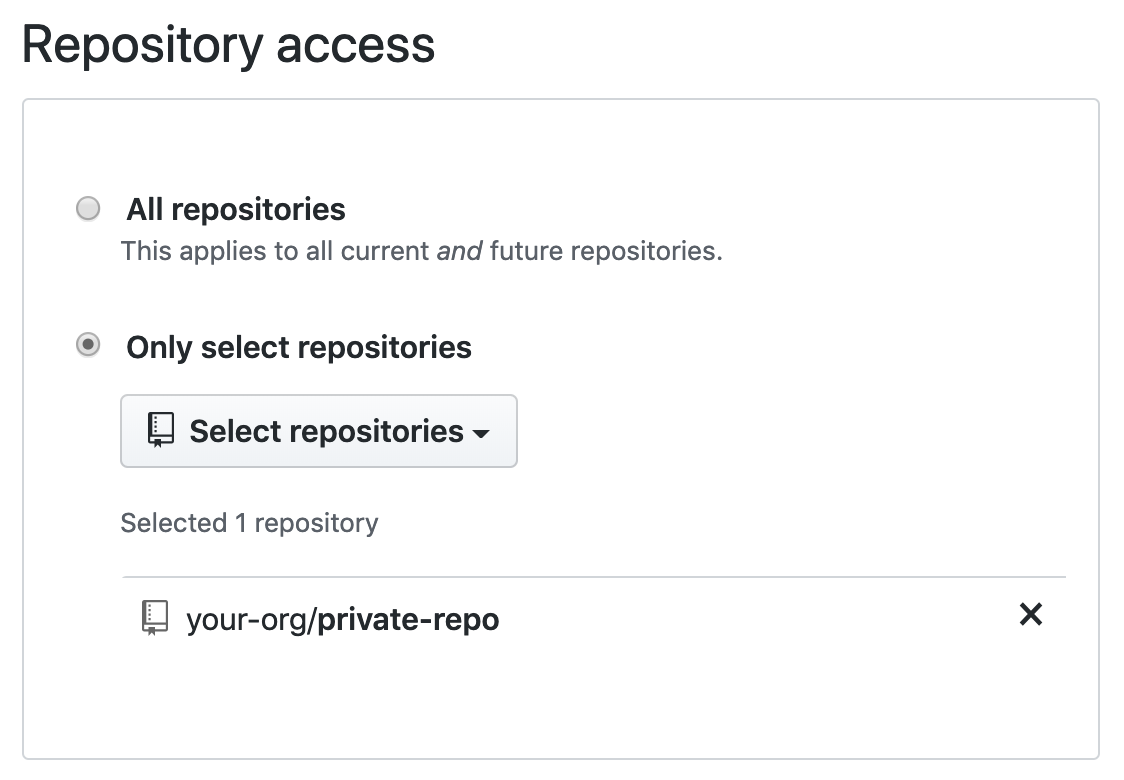
2.
Select which repositories you want to monitor for unintentional exposure of secrets.3.
Rest easy that Secret Audit will help your team keep secrets, secret.
Pricing
Free
- 1 repository
- 5 audits per month
$3/mo
- 10 repositories
- 1,000 audits per month
- Repo-level configuration
$9/mo
- 50 repositories
- 5,000 audits per month
- Repo-level configuration
$99/mo
- Unlimited repositories
- Unlimited audits per month
- Custom post-audit webhooks
- Org-level configuration